Hackers are now using subtitle files to take over devices
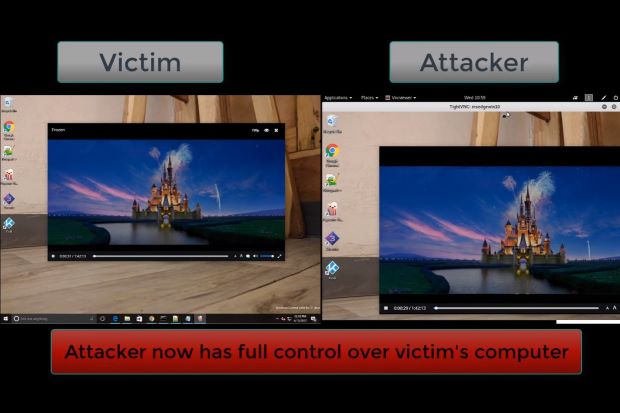 |
The victim's PC can be taken over within
seconds via remote access once the malicious subtitle file is played
alongside a video file. — Check Point
|
According to security research firm Check Point, attackers are now creating malicious files disguised as subtitles, that are then uploaded to popular subtitles repositories widely available on the Internet.
While it’s still safe for users to download the files onto their devices, the attack will happen when users play a video alongside the malicious subtitle file.
According to the demo provided by Check Point, attackers will be able to take over the victim’s device within seconds after the video is played (where the malicious file is executed in the background).
Check Point estimated that over 200 million people around the world are at risk of the attack, making it one of the most widespread, easily accessed and zero-resistance vulnerabilities reported in recent years.
The security firm says that once attackers gain access to the victim’s PC, the possible damage is endless ranging from stealing sensitive information, installing ransomware to mass Denial of Service (DoS) attacks.
If you happen to be one of those who are downloading subtitles on free online sources such as Subscene, YIFY Subtitles and OpenSubtitles, watch out as you might be unknowingly downloading malicious subtitle files.
What makes it so dangerous is the fact that many of the subtitles repositories are treated as trusted sources, allowing anyone to upload subtitles which are then downloaded by millions of users globally.
“The attack vector relies heavily on the poor state of security in the way various media players process subtitle files and the large number of subtitle formats,” according to the blog post by Check Point.
It says that there are over 25 subtitle formats in use, each with unique features and capabilities, along with how the different types of media players make use of these subtitles.
Check Point likens it to similar situations involving fragmented software, resulting in numerous distinct vulnerabilities.
The firm pointed out that four popular media players such as VLC, Kodi, Popcorn Time and Streamio are affected by the vulnerability.
It also believes that a similar vulnerability exists in other media players.
If you happen to be running the older versions of the media players, it’s best to update them right now as the developers have issued fixes on their respective websites.
Source: http://www.thestar.com.my/tech/tech-news/2017/05/24/hackers-are-now-using-subtitle-files-to-take-over-victim-s-device/


